Ted Harrington
Cyber Security Expert
September 12, 2022
If I told you that there is data that shows that higher educational institutions are performing better at security than businesses are, would you believe me?
You wouldn’t?
Well you’re in good company, because I didn’t either.
That is, anyways, until I read the Cyber Security Breaches Survey 2022, a report that was recently published by the United Kingdom’s Department for Digital, Culture, Media & Sport.
-
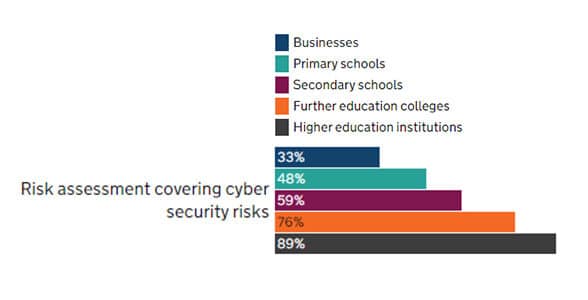
Page after page of graphs seemed to indicate that higher education in the UK was outperforming businesses when it comes to security breaches, such as:
- 100% of higher education institutions assessed the impact and scale of breaches they discovered, while only 73% of businesses did.
- 100% of higher education institutions reported to have up to date malware protection, whereas only 83% of businesses reported the same.
- 100% of higher education institutions have an agreed process to follow for fraudulent emails and websites, whereas only 57% of businesses had the same.
- And much more
-
But then something further shocked me: across the board, higher education reported significantly more breaches – of every type investigated, from DDoS to account takeover to ransomware, and much more.
So, what gives? How could Higher Ed be reportedly doing more of the right things yet producing worse results in terms of breach performance?
As I dug into the data, three things stood out to me that we can learn from this.
TAKEAWAY 1
-
Penetration Testing Isn’t Always Penetration Testing
89% of Higher Ed reported to engage in third party penetration testing, while only 14% of businesses reported the same.
My first reaction to this shocking data point is that it must be wrong. In my experience leading a group of ethical hackers, I have indeed seen that too few companies engage this critical service, but 14% seemed almost comically low. And 89% of Higher Ed seemed almost comically high.
Then I realized what’s probably going on here:
There is an almost grotesque misunderstanding about what security testing even is.
-
As I wrote about in length in my bestseller Hackable: How to Do Application Security Right, the term “penetration testing” has become so widely misused and misunderstood that it almost doesn’t even mean anything anymore.
Some people mean running vulnerability scans, others mean some degree of manual removal of false positives on vulnerability scans, and others mean vulnerability assessments. These each require different levels of time, effort, and money. Each deliver different outcomes.
If we reconsider the data from this report, what it’s probably telling us is that everyone – whether businesses or Higher Ed – are all talking about different things.
TAKEAWAY 2
-
Consider Supply Chain Risk
One of the things that surprised me (in a good way!) about the report was to read that “All types of educational institutions are more likely than businesses to say they have reviewed supplier-related risks to cyber security…”. How cool is that! This is one of the most important, and yet overlooked and misunderstood, parts of the entire security process!
Unfortunately, the data also shows us that more than 64% of Higher Ed do not even consider this issue at all. So there is still a long road to go.
-
Supply Chain Risk – also often referred to as Third Party Risk and/or Vendor Risk (all 3 of which terms mean slightly different things) – addresses the idea that many organizations are attacked not directly but instead through an outside party. Do you remember that massive security breach of the US retailer Target, that became worldwide news not just because 40 million credit cards were stolen but because the CTO and CIO were fired as a result?
That was a big turning point in how security was viewed, because it was now understood to be a leadership issue and not just a technical issue (which has always been true! Except now the world began to notice). Target was breached because one of their vendors was breached, and then those vendor’s credentials provided access that led to the devastating breach.
Third Party Risk Management / Vendor Risk Management (TPRM / VRM) is a discussion that far exceeds the scope of this article but there are some actions you can consider:
-
- If you are a medium to large organization that has many vendors (>100) who supply products and services to you, stop tracking it all via email and spreadsheets, and instead subscribe to a tool that is built specifically for TPRM / VRM. Though there is of course a price to these, it is significantly less than the effort and hassle it takes to manage VRM manually, all while providing better data when you need it, so you can make better decisions.
- If you are a small organization who is the vendor yourself that supplies products or services to a larger organization, make sure to optimize your security questionnaire responses so your customer/partner feels trust and confidence in doing business with you.
(If you don’t know where to start on either of these, contact me and I’ll point you in the direction of some free resources to help)
TAKEAWAY 3
-
Have a Security Champion on the Leadership Team
Perhaps my favorite single sentence in this entire report was “Where there was an individual at senior level with an understanding of cyber security, decision making was more efficient.” When I read this, I audibly shouted “Yes!” and pumped my arms in the air in celebration!
Far too often, security is seen as a technical issue, one that is handled by those working in the bowels of the organization but not something that needs to reach the eyes and ears of the top levels of leadership, who focus on strategy, vision, and mission.
-
But I assure you: security is a leadership issue.
It’s an issue not just because it is the right thing to do (and it is indeed the right thing to do), but simply because it makes good business sense. Although the report I analyzed focused only on this topic in a qualitative sense rather than a quantitative sense, it hit the heart of the matter: security decision-making works better if a security voice is in the room. You can make decisions more efficiently and more effectively.
Here’s an effective way to think about implementing this:
- Hire a Chief Information Security Officer (or someone who is in charge of security, even if you don’t use that title)
- Ensure that person’s top (and ideally, only) responsibility is security. They should not also have responsibilities for system functionality, which could at times conflict with the security priority
- Have that person report directly to the President (or CEO or whatever is the top ranking title at your organization). There should not be an additional reporting level to the top, such as reporting to a CIO or CTO
Now it’s time to take action on this. Whether or not you read the report (and I recommend you do; it’s a quick read with a lot more data than I included here), make sure you go back to your organization and do 3 things:
- Understand security testing and implement the right type
- Evolve your approach to managing risk introduced by third parties
- Get a security voice in the room with leadership
If you implement these ideas, you’ll be able to make good strides on building better, more secure systems.

About the Author
Ted Harrington is the #1 best selling author of HACKABLE: How to Do Application Security Right, and the Executive Partner at Independent Security Evaluators (ISE), the company of ethical hackers famous for hacking cars, medical devices, web applications, and password managers. To get help with security consulting and security assessments, or to book Ted to keynote your next event, visit https://www.tedharrington.com.