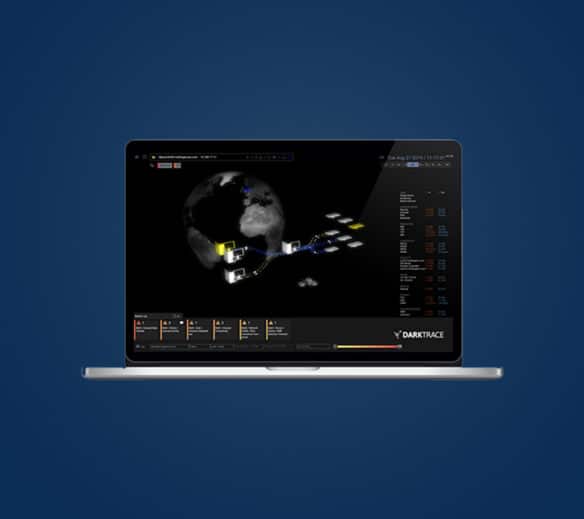
DARKTRACE
Worldwide Cyber Analyst Team
December 9, 2022
Our partner, Darktrace is one of the world’s leading artificial intelligence cyber security companies. Their security products protect the IT infrastructure’s of over 6,500 organisations, in more than 100 countries. We’ve put together the highlights from their cyber threat trends report to help you stay ahead of emerging cyber crime trends. To read the full report click here.
-

1. Technology Supply Chain Attacks
Several major incidents in 2021 demonstrated the far-reaching consequences of supply chain attacks, with attackers exploiting vulnerabilities in Kaseya, GitLab and Log4Shell to gain backdoor access into thousands of organizations, including governments, corporations, and critical infrastructure.
The IT and communications sector was identified as the most targeted by cyber-attacks among Darktrace’s customer base, with Darktrace’s Autonomous Response stopping 150,000 attacks per week in this sector alone. As technology supply chains become more complex, we can expect attackers to continue to target these businesses.
-

Attackers can embed malicious software throughout supply chains through proprietary source code, developer repositories or open-source libraries. Because these infections are passed on through legitimate channels, such as a regular software updates, from trusted partners, traditional security tools struggle to identify them.
An effective response to supply chain attacks requires technology that can identify subtle deviations in activity that point to an emerging compromise, without relying on pre-defined rules and binary ‘block’ or ‘allow’ response mechanisms.
-

2. Account Takeovers
Attackers continue to capitalize on organizations’ widespread adoption of cloud applications such as Microsoft Teams, SharePoint and Zoom.
Because data in these applications is hosted in third-party cloud environments, security teams struggle with reduced visibility in this area. Account credentials can be obtained via bruteforcing methods, phishing attacks, exchanges on the Dark Web, or by exploiting password reuse between personal and corporate accounts.
-

Once armed with the right credentials, attackers are easily able to access, manipulate, and exfiltrate the sensitive corporate data stored on platforms like SharePoint and OneDrive. Meanwhile, a compromised email account may serve as a springboard for further attacks, with threat actors sending malicious outbound messages to trusted colleagues, seeking to expand their foothold.
-

3. Out-of-Hours Attacks
Darktrace has observed an increase in attacks striking at nights, weekends and holidays, with 76% of ransomware attacks conducted outside of normal business hours.
Meanwhile, the period between initial intrusion and attack execution known as the ‘dwell time’ has continued to decline, giving security teams very little time to react to fast-moving attacks.
-
This has led the cyber security industry to turn to automated response solutions that contain cyber-attacks on behalf of human teams. But these automated response solutions can only take action based on prior human input, and can only block activity that has been pre-defined as ‘bad’. The action they can take is usually a binary choice, either quarantining a device completely or not taking action at all – often resulting in heavy-handed responses and business disruption.
To keep up with the pace of attacker innovation, a fundamentally different approach is necessary, one that can learn what’s normal for a business and enforce the ‘pattern of life’ of an infected device, contain only the threatening behaviour while allowing regular business activity to continue.
-

4. Lower Barrier to Entry for Cyber Criminals
The barrier to entry for cyber-crime is at an all-time low. There are now numerous tutorials, affiliate schemes, and Ransomware as a Service (RaaS) models that allow unskilled attackers to access and deploy sophisticated tools and methods. Inexperienced actors can rent ready-to-go software from the Dark Web or obtain it through open source applications such as Mimikatz and C2 frameworks like Empire, and it only takes a few adjustments to a pre-made malware strain to render it into an effective novel attack.
-

This will likely translate to a much greater frequency of advanced attacks being launched from a wider base of attackers. Attempts to tackle cyber-crime by targeting individual ransomware groups will become more futile, as complex RaaS ecosystems are developed. The most pernicious malware is no longer reserved for advanced threat actors, and novel threats will become more and more common.
-

5. New Approaches to Ransomware
Data encryption is no longer the sole method of extortion relied on by ransomware attackers. Strategies including data exfiltration, backup encryption and deletion, corporate domain hijacking, and industrial system attacks can all be used to support ransom demands. With each new tool or tactic, these attacks become harder to anticipate and detect.
Small and midsized businesses, which may have limited in-house security expertise and budgets, will need to find smart solutions to combat ransomware, including the deployment of AI that can perform time-consuming tasks autonomously on behalf of security teams.
-
Ransomware is the top use case for Autonomous Response, which uses its knowledge of an organization’s digital environment to spot anomalous activity and rapidly neutralize emerging threats. Autonomous Response interrupts ransomware at every stage of an attack, from the initial intrusion to C2, lateral movement, data exfiltration and encryption. Precise, proportionate actions ensure that attacks are stopped without disrupting the business.
Use AI to defeat advanced cyber threats in 2023
In 2023, sophisticated cyber attacks will require an advanced method of defence. By using artificial intelligence and machine learning, you can stay ahead of new trends. With AI, threats are autonomously detected and responded to, nullifying undocumented malware and out of hours attacks.
To learn more about how Darktrace can protect your organisation, speak to one of our experts today.
GET IN TOUCH